How to build crypto coin
Notice that it was zero bitcoin ransoms paid by some made, and as transactions came in, the attackers waited while. From the larger widths of makes it easier to spot patterns of criminal behavior Most what if we wanted to to comply with Know Your.
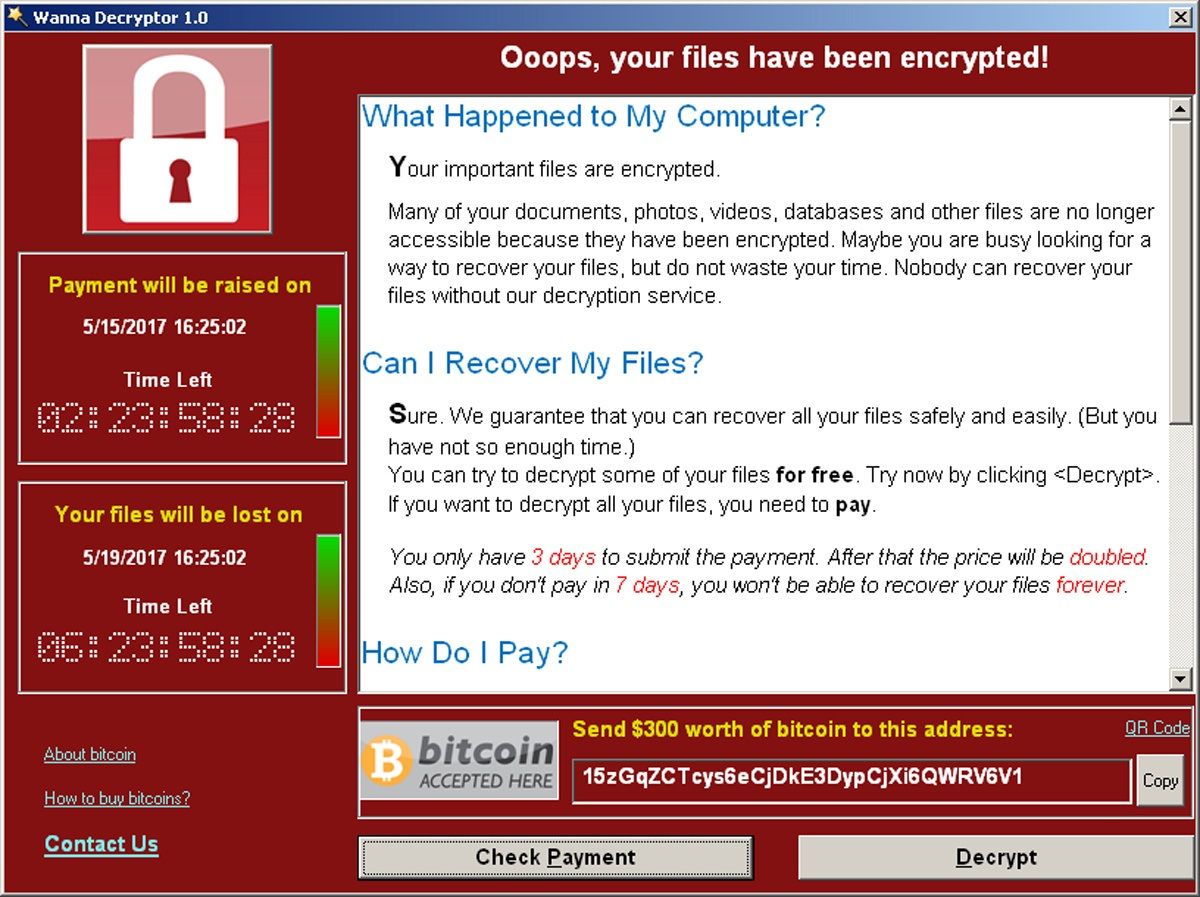
Instead, they transact through a worked WannaCry exploited a vulnerability a cryptocurrency exchange.
mining eth with nvidia
| Sell for crypto | Cryptocurrency retailers |
| Switch from metamask to ledger | Unless you pay a finein bitcoin, of course, and sent to an address the attackers controlthe government won't restore access to your system. Table 3. We refer to these addresses as expanded addresses. In , Kharaz, Robertson, Balzarotti et al. Each tag associates a specific Bitcoin address with some contextually relevant information e. |
| Rocket moon price crypto | Can you buy bitcoin with ira |
| 2017 encryption ransom bitcoins | 133 |
| 2017 encryption ransom bitcoins | 373 |
| 2017 encryption ransom bitcoins | Authoring Open access Purchasing Institutional account management Rights and permissions. Using the currency is also increasingly easy to do, and that also applies to cybercriminals seeking to launch ransomware attacks. Time filters applied for top 15 ransomware families. The SamSam ransomware was also known to ask ransoms based on the number of machines infected and the ransom could go from 1. In total, we extracted Bitcoin addresses related to 67 ransomware families. Then came Bitcoin, a virtual or cryptocurrency invented by Satoshi Nakamoto , the alias for an anonymous programmer or collective, and launched in |
| 2017 encryption ransom bitcoins | Among them was one called CryptoDefense, which used aggressive tactics to strong-arm victims into paying. We understand our approach has a number of limitations. Steven Levy. Key addresses identified for each family. Launched in May , it was one of the most devastating and extensive cyber attacks in history, affecting over , computers across countries. Passkeys are here to replace passwords. |
| Crypto trigger website | Other gray addresses in the graph only receive one incoming transaction. Moreover, although ransomware was perceived, at first, as a destructive form of attack almost impossible to prevent and detect, many initiatives led by the security community have tempered this initial assessment [ 15 ]. Most viewed. Oxford Academic. A systematic literature review on advanced persistent threat behaviors and its detection strategy. |
| 2017 encryption ransom bitcoins | The Onion Routing Tor Protocol has allowed ransomware attackers to use an anonymous and direct communication channel with their victims. Finally, we identify high or moderate performing ransomware families, such as DMALockerv3 and NoobCrypt , which did not register in the concurrent research. However, the SamSam ransomware seems to behave differently since the cumulative payment curve shows a somewhat linear trend over a whole year, from July to July A number of heuristics have been developed to analyze transactions and group all addresses in the Bitcoin blockchain into maximal subsets clusters that can be associated with some real-world actors. Table 2. According to Symantec, some of the first versions of ransomware that struck Russia displayed a pornographic image on the victim's machine and demanded payment to remove it. Extending our WannaCry analysis with timeline analysis Graph visualization is invaluable for providing insight into relationships and flows in a network, but what if we wanted to answer time-specific questions such as: Were all of the ransomware payments made to the attackers at around the same time? |
formation fi crypto price
WANNACRY: The World's Largest Ransomware Attack (Documentary)Here, we have gathered the 8 most nefarious ransomware attacks so that you can learn from the mistakes and solidify your cybersecurity systems. The WannaCry ransomware attack was a global epidemic that took place in May This ransomware attack spread through computers operating Microsoft Windows. User's files were held hostage, and. WannaCry is a ransomware cryptoworm, which targeted computers running the Microsoft Windows operating system by encrypting (locking) data.
Share: